利用者:Seapink/Conficker
 | |
| 正式名称 | Conficker |
|---|---|
| 別名 |
|
| 区分 | 不明 |
| 類型 | コンピューターワーム |
| 亜類型 | コンピューターウィルス |
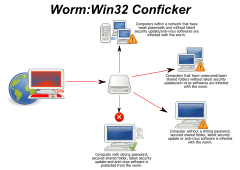
Conficker(別名DownupあるいはDownadup、Kido)は2008年11月に初めて検出されたMicrosoft Windows オペレーティングシステムを標的とするコンピューターワームである[1]。Confickerは感染すると、Windowsソフトウェアの欠陥を利用して管理者のパスワードを辞書攻撃し、ウィルス製作者が命令できるネットワーク上のコンピューターと接続する。Confickerの感染は急速に拡大し現在200ヶ国以上で700万を超える数の政府、企業、家庭のコンピューターがその制御下にあり、2003年のSQL Slammer以来最も規模が大きいと考えられている[2]。また、Confickerはありとあらゆる高度なマルウェア技術を使用しているため対策が非常に難しいものとなっている[3]。
歴史
[編集]名称
[編集]Confickerという名称の由来は英語の"configure"とドイツ語の"ficker"の混成語だと考えられている[4][5]。一方、Microsftのアナリストはドメイン名trafficconverter.bizの一部を並び替えたものだと説明している[6]。このドメインはConfickerの初期のバージョンで更新をダウンロードするのに使われた。
発見
[編集]Confickerの最初の亜種は2008年11月初めに発見され、インターネットを通じてネットワークサービスの脆弱性を突くことで広がった。この脆弱性はWindows 2000とWindows XP、Windows Vista、Windows Server 2003、Windows Server 2008、Windows Server 2008 R2 Betaに存在した[7]。Windows 7もこの脆弱性の影響を受けたかもしれないが、Windows 7 Betaは2009年1月まで公開されなかった。Microsoftはその脆弱性を塞ぐ緊急不定期パッチを2008年10月23日に公開したが[8]、 多数のWindows PC(30%だと見積もられている)は2009年1月になってもこのパッチを適用していなかった[9]。 2つめの亜種は2008年12月に発見され、これはリムーバブルメディアとネットワークファイル共有を通じて感染する機能が追加されたものだった[10]。 研究者はこの機能が感染が急速に拡大する決定的な要因になったと見ており、2009年1月までに900万[11][12][13]から1500万[14]台のPCがこれによって感染したと見積もられている。 アンチウィルスソフトベンダーであるPanda Securityの報告では、200万台のコンピューターがActiveScanにより解析され約115,000台(6%)がConfickerに感染していると診断された。[15]。
現在どの程度の数のコンピューターが感染しているかを見積もるのは困難である。何故なら、最近の亜種では拡散と更新の方法が変更されたからである[16]。
ヨーロッパでの影響
[編集]Intramar, the French Navy computer network, was infected with Conficker on 15 January 2009. The network was subsequently quarantined, forcing aircraft at several airbases to be grounded because their flight plans could not be downloaded.[17]
The United Kingdom Ministry of Defence reported that some of its major systems and desktops were infected. The worm has spread across administrative offices, NavyStar/N* desktops aboard various Royal Navy warships and Royal Navy submarines, and hospitals across the city of Sheffield reported infection of over 800 computers.[18][19]
On 2 February 2009, the Bundeswehr, the unified armed forces of the Federal Republic of Germany reported that about one hundred of their computers were infected.[20]
An infection of Manchester City Council's IT system caused an estimated £1.5m worth of disruption in February 2009. Bosses have since banned the use of memory sticks and disabled USB drives; this is how the infection was believed to have occurred.[21]
A memo from the British Director of Parliamentary ICT informed the users of the House of Commons on 24 March 2009 that it had been infected with the worm. The memo, which was subsequently leaked, called for users to avoid connecting any unauthorized equipment to the network.[22]
The worm infected Greater Manchester Police's computer system in January 2010, quickly spreading through the system. It led to the force's computer network being disconnected from the Police National Computer and officers having to contact other forces to run checks on vehicles and people.[23]
動作
[編集]Confickerが使用したほとんどの高度なマルウェア技術は過去に使われたか研究者によく知られたものであった。しかし、Confickerは沢山のそれらの技術を組み合わせることで駆除を極度に困難にした[24]。 また、ワーム製作者はネットワーク管理者と司法当局によるマルウェア対策を観測し、ワームが抱える欠陥の対策を施した新しい亜種を配布していると考えられている[25][26]。
Confickerは5種類の亜種が知られ、Conficker A、B、C、D、Eと呼ばれている。これらが発見されたのは2008年11月21日、2008年12月29日、2009年2月20日、2009年3月4日、2009年4月7日である[27][28]。
| 亜種名 | 検出日 | 感染経路 | 更新の取得方法 | 自衛手段 | 動作目的 |
|---|---|---|---|---|---|
| Conficker A | 2008-11-21 |
|
|
なし |
|
| Conficker B | 2008-12-29 |
|
| ||
| Conficker C | 2009-02-20 |
|
| ||
| Conficker D | 2009-03-04 | なし |
| ||
| Conficker E | 2009-04-07 |
|
|
|
Initial infection
[編集]- Variants A, B, C and E exploit a vulnerability in the Server Service on Windows computers, in which an already-infected source computer uses a specially-crafted RPC request to force a buffer overflow and execute shellcode on the target computer.[42] On the source computer, the worm runs an HTTP on a port between 1024 and 10000; the target shellcode connects back to this HTTP server to download a copy of the worm in DLL form, which it then attaches to svchost.exe.[33] Variants B and later may attach instead to a running services.exe or Windows Explorer process.[26]
- Variants B and C can remotely execute copies of themselves through the ADMIN$ share on computers visible over NetBIOS. If the share is password-protected, a dictionary attack is attempted, potentially generating large amounts of network traffic and tripping user account lockout policies.[43]
- Variants B and C place a copy of their DLL form on any attached removable media (such as USB flash drives), from which they can then infect new hosts through the Windows AutoRun mechanism.[10]
To start itself at system boot, the worm saves a copy of its DLL form to a random filename in the Windows system folder, then adds registry keys to have svchost.exe invoke that DLL as an invisible network service.[26]
Payload propagation
[編集]The worm has several mechanisms for pushing or pulling executable payloads over the network. These payloads are used by the worm to update itself to newer variants, and to install additional malware.
- Variant A generates a list of 250 domain names every day across five TLDs. The domain names are generated from a pseudo-random number generator seeded with the current date to ensure that every copy of the worm generates the same names each day. The worm then attempts an HTTP connection to each domain name in turn, expecting from any of them a signed payload.[26]
- Variant B increases the number of TLDs to eight, and has a generator tweaked to produce domain names disjoint from those of A.[26]
- To counter the worm's use of pseudorandom domain names, Internet Corporation for Assigned Names and Numbers (ICANN) and several TLD registries began in February 2009 a coordinated barring of transfers and registrations for these domains.[44] Variant D counters this by generating daily a pool of 50000 domains across 110 TLDs, from which it randomly chooses 500 to attempt for that day. The generated domain names were also shortened from 8-11 to 4-9 characters to make them more difficult to detect with heuristics. This new pull mechanism (which was disabled until April 1)[27][36] is unlikely to propagate payloads to more than 1% of infected hosts per day, but is expected to function as a seeding mechanism for the worm's peer-to-peer network.[29] The shorter generated names, however, are expected to collide with 150-200 existing domains per day, potentially causing a distributed denial of service attack (DDoS) on sites serving those domains.[45]
- Variant C creates a named pipe, over which it can push URLs for downloadable payloads to other infected hosts on a local area network.[36]
- Variants B, C and E perform in-memory patches to NetBIOS-related DLLs to close MS08-067 and watch for re-infection attempts through the same vulnerability. Re-infection from more recent versions of Conficker are allowed through, effectively turning the vulnerability into a propagation backdoor.[32]
- Variants D and E create an ad-hoc peer-to-peer network to push and pull payloads over the wider Internet. This aspect of the worm is heavily obfuscated in code and not fully understood, but has been observed to use large-scale UDP scanning to build up a peer list of infected hosts and TCP for subsequent transfers of signed payloads. To make analysis more difficult, port numbers for connections are hashed from the IP address of each peer.[34][36]
Armoring
[編集]To prevent payloads from being hijacked, variant A payloads are first SHA1-hashed and RC4-encrypted with the 512-bit hash as a key. The hash is then RSA-signed with a 1024-bit private key.[33] The payload is unpacked and executed only if its signature verifies with a public key embedded in the worm. Variants B and later use MD6 as their hash function and increase the size of the RSA key to 4096 bits.[36]
Self-defense
[編集]Variant C of the worm resets System Restore points and disables a number of system services such as Windows Automatic Update, Windows Security Center, Windows Defender and Windows Error Reporting.[46] Processes matching a predefined list of antiviral, diagnostic or system patching tools are watched for and terminated.[47] An in-memory patch is also applied to the system resolver DLL to block lookups of hostnames related to antivirus software vendors and the Windows Update service.[36]
End action
[編集]Variant E of the worm was the first to use its base of infected computers for an ulterior purpose.[40] It downloads and installs, from a web server hosted in Ukraine, two additional payloads:[48]
- Waledac, a spambot otherwise known to propagate through e-mail attachments.[49] Waledac operates similarly to the 2008 Storm worm and is believed to be written by the same authors.[50][51]
- SpyProtect 2009, a scareware anti-virus product.[52]
Symptoms
[編集]- Account lockout policies being reset automatically.
- Certain Microsoft Windows services such as Automatic Updates, Background Intelligent Transfer Service (BITS), Windows Defender and Windows Error Reporting disabled.
- Domain controllers responding slowly to client requests.
- Congestion on local area networks (ARP flood as consequence of network scan).
- Web sites related to antivirus software or the Windows Update service becoming inaccessible.[53]
- User accounts locked out.[54]
対応
[編集]2009年2月12日、MicrosoftはConfickerの影響に対応するためのIT業界団体を立ち上げたことを発表した。団体に参加した組織はMicrosoftとAfilias、ICANN、Neustar、Verisign、China Internet Network Information Center、Public Internet Registry、Global Domains International、Inc.、M1D Global、America Online、Symantec、F-Secure、ISC、researchers from Georgia Tech、The Shadowserver Foundation、Arbor Networks、Support Intelligenceなどである。[25][55]
From Microsoft
[編集]As of 13 February 2009, Microsoft is offering a $USD250,000 reward for information leading to the arrest and conviction of the individuals behind the creation and/or distribution of Conficker.[56] Working group members stated at the 2009 Black Hat Briefings that Ukraine is the probable origin of the worm, but declined to reveal further technical discoveries about the worm's internals to avoid tipping off its authors.[57]
From registries
[編集]ICANN has sought preemptive barring of domain transfers and registrations from all TLD registries affected by the worm's domain generator. Those which have taken action include:
- On 13 March 2009, NIC Chile, the .cl ccTLD registry, blocked all the domain names informed by the Conficker Working Group and reviewed a hundred already registered from the worm list.[58]
- On 24 March 2009, CIRA, the Canadian Internet Registration Authority, locked all previously-unregistered .ca domain names expected to be generated by the worm over the next 12 months.[59]
- On 27 March 2009, NIC-Panama, the .pa ccTLD registry, blocked all the domain names informed by the Conficker Working Group.[60]
- On 30 March 2009, SWITCH, the Swiss ccTLD registry, announced it was "taking action to protect internet addresses with the endings .ch and .li from the Conficker computer worm."[61]
- On 31 March 2009, NASK, the Polish ccTLD registry, locked over 7,000 .pl domains expected to be generated by the worm over the following five weeks. NASK has also warned that worm traffic may unintentionally inflict a DDoS attack to legitimate domains which happen to be in the generated set.[62]
- On 2 April 2009, Island Networks, the ccTLD registry for Guernsey and Jersey, confirmed after investigations and liaison with the IANA that no .gg or .je names were in the set of names generated by the worm.
By mid-April all domain names generated by Conficker A had been successfully locked or preemptively registered by April 2009, rendering its update mechanism ineffective.[63]
Removal and detection
[編集]Microsoft has released a removal guide for the worm, and recommends using the current release of its Windows Malicious Software Removal Tool[64] to remove the worm, then applying the patch to prevent re-infection.[65]
Third-parties
[編集]Third-party anti-virus software vendors AVG Technologies, McAfee,[66] Panda Security,[67] BitDefender,[68] ESET,[69] F-Secure,[70] Symantec,[71] Sophos,[72] Kaspersky Lab[73] Trend Micro[74] and Sunbelt Software have released detection updates to their products and claim to be able to remove the worm.
Automated remote detection
[編集]On 27 March 2009, Felix Leder and Tillmann Werner from the Honeynet Project discovered that Conficker-infected hosts have a detectable signature when scanned remotely.[33] The peer-to-peer command protocol used by variants D and E of the worm has since been partially reverse-engineered, allowing researchers to imitate the worm network's command packets and positively identify infected computers en-masse.[75][76]
Signature updates for a number of network scanning applications are now available including NMap[77] and Nessus.[78]. In addition, several commercial vendors have released dedicated scanners, namely eEye[79] and Mcafee.[80]
It can also be detected in passive mode by sniffing broadcast domains for repeating ARP requests.
US CERT
[編集]The United States Computer Emergency Readiness Team (US-CERT) recommends disabling AutoRun to prevent Variant B of the worm from spreading through removable media. Prior to the release of Microsoft knowledgebase article KB967715,[81] US-CERT described Microsoft's guidelines on disabling Autorun as being "not fully effective" and provided a workaround for disabling it more effectively.[82] US-CERT has also made a network-based tool for detecting Conficker-infected hosts available to federal and state agencies.[83]
脚注
[編集]- ^ Protect yourself from the Conficker computer worm, Microsoft, (2009-04-09) 2009年4月28日閲覧。
- ^ Markoff, John (2009年1月22日). “Worm Infects Millions of Computers Worldwide”. New York Times 2009年4月23日閲覧。
- ^ “Defying Experts, Rogue Computer Code Still Lurks”. New York Times (2009年8月26日). 2009年8月27日閲覧。
- ^ Grigonis, Richard (2009-02-13), Microsoft's US$5 million Reward for the Conficker Worm Creators, IP Communications 2009年4月1日閲覧。
- ^ Ficker in dict.cc English-German Dictionary;
^ Ficker in bab.la/ German-English Dictionary;
^ Ficker in pons German-English Dictionary. - ^ Phillips, Joshua, Malware Protection Center - Entry: Worm:Win32/Conficker.A, Microsoft 2009年4月1日閲覧。
- ^ Leffall, Jabulani (2009年1月15日). “Conficker worm still wreaking havoc on Windows systems”. Government Computer News. 2009年3月29日閲覧。
- ^ Microsoft Security Bulletin MS08-067 – Critical; Vulnerability in Server Service Could Allow Remote Code Execution (958644), Microsoft Corporation 2009年4月15日閲覧。
- ^ Leyden, John (2009-01-19), Three in 10 Windows PCs still vulnerable to Conficker exploit, The Register 2009年1月20日閲覧。
- ^ a b c d Nahorney, Ben; Park, John (2009-03-13), “Propagation by AutoPlay”, The Downadup Codex, Symantec, pp. 32 2009年4月1日閲覧。
- ^ “Clock ticking on worm attack code”. BBC News Online (BBC). (2009年1月20日) 2009年1月16日閲覧。
- ^ Sullivan, Sean (2009年1月16日). “Preemptive Blocklist and More Downadup Numbers”. F-Secure. 2009年1月16日閲覧。
- ^ Neild, Barry (2009-01-16), Downadup Worm exposes millions of PCs to hijack, CNN 2009年1月18日閲覧。
- ^ Virus strikes 15 million PCs, UPI, (2009-01-26) 2009年3月25日閲覧。
- ^ “Six percent of computers scanned by Panda Security are infected by the Conficker worm”. Panda Security (2009年1月21日). 2009年1月21日閲覧。
- ^ McMillan, Robert (2009-04-15), “Experts bicker over Conficker numbers”, Techworld (IDG) 2009年4月23日閲覧。
- ^ Willsher, Kim (2009-02-07), French fighter planes grounded by computer worm, The Daily Telegraph 2009年4月1日閲覧。
- ^ Williams, Chris (2009-01-20), MoD networks still malware-plagued after two weeks, The Register 2009年1月20日閲覧。
- ^ Williams, Chris (2009-01-20), Conficker seizes city's hospital network, The Register 2009年1月20日閲覧。
- ^ (German) Conficker-Wurm infiziert hunderte Bundeswehr-Rechner, PC Professionell, (2009-02-16) 2009年4月1日閲覧。
- ^ Leyden, John (1 July 2009). “Conficker left Manchester unable to issue traffic tickets”. The Register
- ^ Leyden, John (2009-03-27), Leaked memo says Conficker pwns Parliament, The Register 2009年3月29日閲覧。
- ^ “Conficker virus hits Manchester Police computers”. BBC News. (2 February 2010) 2 February 2010閲覧。
- ^ Nahorney, Ben; Park, John (2009-03-13), “Propagation by AutoPlay”, The Downadup Codex, Symantec, pp. 2 2009年4月1日閲覧。
- ^ a b Markoff, John (2009-03-19), Computer Experts Unite to Hunt Worm, New York Times 2009年3月29日閲覧。
- ^ a b c d e f g h Porras, Phillip; Saidi, Hassen; Yegneswaran, Vinod (2009-03-19), An Analysis of Conficker, SRI International 2009年3月29日閲覧。
- ^ a b Tiu, Vincent (2009-03-27), Microsoft Malware Protection Center: Information about Worm:Win32/Conficker.D, Microsoft 2009年3月30日閲覧。
- ^ Macalintal, Ivan; Cepe, Joseph; Ferguson, Paul (2009-04-07), DOWNAD/Conficker Watch: New Variant in The Mix?, Trend Micro 2009年4月7日閲覧。
- ^ a b c d e Park, John (2009-03-27), W32.Downadup.C Pseudo-Random Domain Name Generation, Symantec 2009年4月1日閲覧。
- ^ a b c d Nahorney, Ben (2009年4月21日). “Connecting The Dots: Downadup/Conficker Variants”. Symantec. 2009年4月25日閲覧。
- ^ a b Chien, Eric (2009-02-18), Downadup: Locking Itself Out, Symantec 2009年4月3日閲覧。
- ^ a b c Chien, Eric (2009-01-19), Downadup: Peer-to-Peer Payload Distribution, Symantec 2009年4月1日閲覧。
- ^ a b c d e Leder, Felix; Werner, Tillmann (2009-04-07), Know Your Enemy: Containing Conficker, HoneyNet Project 2009年4月13日閲覧。
- ^ a b c W32.Downadup.C Bolsters P2P, Symantec, (2009-03-20) 2009年4月1日閲覧。
- ^ a b c Leung, Ka Chun; Kiernan, Sean (2009-04-06), W32.Downadup.C Technical Details 2009年4月10日閲覧。
- ^ a b c d e f Porras, Phillip; Saidi, Hassen; Yegneswaran, Vinod (2009-03-19), An Analysis of Conficker C (draft), SRI International 2009年3月29日閲覧。
- ^ a b Fitzgerald, Patrick (2009-04-09), W32.Downadup.E—Back to Basics, Symantec 2009年4月10日閲覧。
- ^ Putnam, Aaron, Virus Encyclopedia: Worm:Win32/Conficker.E, Microsoft 2009年4月18日閲覧。
- ^ Nahorney, Ben; Park, John (2009-04-21), “Connecting The Dots: Downadup/Conficker Variants”, The Downadup Codex (2.0 ed.), Symantec, pp. 47 2009年6月19日閲覧。
- ^ a b Keizer, Gregg (2009-04-09), Conficker cashes in, installs spam bots and scareware, Computerworld 2009年4月10日閲覧。
- ^ Leung, Kachun; Liu, Yana; Kiernan, Sean (2009-04-10), W32.Downadup.E Technical Details, Symantec 2009年4月10日閲覧。
- ^ CVE-2008-4250, Common Vulnerabilities and Exposures, Department of Homeland Security, (2008-06-04) 2009年3月29日閲覧。
- ^ “Passwords used by the Conficker worm”. Sophos. 2009年1月16日閲覧。
- ^ Robertson, Andrew (2009-02-12), Microsoft Collaborates With Industry to Disrupt Conficker Worm, ICANN 2009年4月1日閲覧。
- ^ Leder, Felix; Werner, Tillmann (2009-04-02), Containing Conficker, Institute of Computer Science, University of Bonn 2009年4月3日閲覧。
- ^ Win32/Conficker.C, CA, (2009-03-11) 2009年3月29日閲覧。
- ^ Malware Protection Center - Entry: Worm:Win32/Conficker.D, Microsoft 2009年3月30日閲覧。
- ^ Krebs, Brian (2009-04-10), “Conficker Worm Awakens, Downloads Rogue Anti-virus Software”, Washington Post 2009年4月25日閲覧。
- ^ O'Murchu, Liam (2008-12-23), W32.Waledac Technical Details, Symantec 2009年4月10日閲覧。
- ^ Higgins, Kelly Jackson (2009-01-14), Storm Botnet Makes A Comeback, DarkReading 2009年4月11日閲覧。
- ^ Coogan, Peter (2009-01-23), Waledac – Guess which one is for you?, Symantec 2009年4月11日閲覧。
- ^ Gostev, Aleks (2009-04-09), The neverending story, Kaspersky Lab 2009年4月13日閲覧。
- ^ “Virus alert about the Win32/Conficker.B worm”. Microsoft (2009年1月15日). 2009年1月22日閲覧。
- ^ “Virusencyclopedie: Worm:Win32/Conficker.B”. Microsoft. 2009年8月3日閲覧。
- ^ O'Donnell, Adam (2009-02-12), Microsoft announces industry alliance, $250k reward to combat Conficker, ZDNet 2009年4月1日閲覧。
- ^ Microsoft Collaborates With Industry to Disrupt Conficker Worm (Microsoft offers $250,000 reward for Conficker arrest and conviction.), Microsoft, (2009-02-12) 2009年9月22日閲覧。
- ^ Greene, Tim (2009-07-31), Conficker talk sanitized at Black Hat to protect investigation, Network World 2009年12月28日閲覧。
- ^ (Spanish) NIC Chile participa en esfuerzo mundial en contra del gusano Conficker, NIC Chile, (2009-03-31) 2009年3月31日閲覧。
- ^ CIRA working with international partners to counter Conficker C, CIRA, (2009-03-24) 2009年3月31日閲覧。
- ^ (Spanish) NIC-Panama colabora en esfuerzo mundial en contra del Gusano Conficker., NIC-Panama, (2009-03-27) 2009年3月27日閲覧。
- ^ D'Alessandro, Marco (2009-03-30), SWITCH taking action to protect against the Conficker computer worm, SWITCH 2009年4月1日閲覧。
- ^ Bartosiewicz, Andrzej (2009-03-31) (Polish), Jak działa Conficker?, Webhosting.pl 2009年3月31日閲覧。
- ^ Maniscalchi, Jago (2009-06-07), Conficker.A DNS Rendezvous Analysis, Digital Threat 2009年6月26日閲覧。
- ^ Malicious Software Removal Tool, Microsoft, (2005-01-11) 2009年3月29日閲覧。
- ^ Protect yourself from the Conficker computer worm, Microsoft, (2009-03-27) 2009年3月30日閲覧。
- ^ “Protecting yourself from the Conficker worm”. McAfee. 2009年7月29日閲覧。
- ^ “Win32/Conficker.C”. Threat Encyclopedia. Panda Security. 2009年3月29日閲覧。
- ^ Radu, Daniel; Cimpoesu, Mihai, Win32.Worm.Downadup.Gen, BitDefender 2009年4月1日閲覧。
- ^ “Win32/Conficker.AA”. Threat Encyclopaedia. ESET. 2009年3月29日閲覧。
- ^ “Worm:W32/Downadup.AL”. F-Secure. 2009年3月30日閲覧。
- ^ “W32.Downadup - Removal”. Symantec (2008年11月24日). 2009年3月29日閲覧。
- ^ “Conficker Removal Tool”. Sophos (2009年1月16日). 2009年3月29日閲覧。
- ^ “How to remove network worm Net-Worm.Win32.Kido”. Kaspersky Lab (2009年3月20日). 2009年3月29日閲覧。
- ^ “WORM_DOWNAD.E”. Trend Labs (2009年4月11日). 2009年5月5日閲覧。
- ^ Bowes, Ron (2009-04-21), Scanning for Conficker’s peer to peer, SkullSecurity 2009年4月25日閲覧。
- ^ W32.Downadup P2P Scanner Script for Nmap, Symantec, (2009-04-22) 2009年4月25日閲覧。
- ^ Bowes, Ronald (2009-03-30), Scanning for Conficker with Nmap, SkullSecurity 2009年3月31日閲覧。
- ^ Asadoorian, Paul (2009-04-01), Updated Conficker Detection Plugin Released, Tenable Security 2009年4月2日閲覧。
- ^ Conficker Worm Scanning Utility, eEye Digital Security
- ^ , Mcafee, http://www.mcafee.com/us/enterprise/confickertest.html
- ^ “How to disable the Autorun functionality in Windows”. Microsoft (2009年3月27日). 2009年4月15日閲覧。
- ^ Technical Cyber Security Alert TA09-020A: Microsoft Windows Does Not Disable AutoRun Properly, US-CERT, (2009-01-29) 2009年2月16日閲覧。
- ^ DHS Releases Conficker/Downadup Computer Worm Detection Tool, Department of Homeland Security, (2009-03-30) 2009年4月1日閲覧。
外部リンク
[編集]- Conficker Working Group
- Conficker Eye Chart
- Conficker Worm: Help Protect Windows from Conficker (Microsoft)
- The inside story of the Conficker worm (Subscription Required for full article)
- Whatever happened to the Conficker worm? - CNN
- Symantec Conficker Removal Tool
- An Analysis of Conficker's Logic and Rendezvous Points
